In a world where technology is evolving at a breathtaking pace, the importance of cybersecurity cannot be overstated. Every day, cybersecurity threats loom large as malicious actors seek to exploit vulnerabilities in both personal and organizational systems. Protecting data has never been more critical, with breaches affecting millions of individuals and countless businesses worldwide. Adopting best cybersecurity practices, such as regular software updates and robust password management, is essential in safeguarding against these evolving threats. Moreover, fostering an awareness of cyber hygiene can empower individuals and organizations alike to minimize risks and ensure a safer digital experience.
As we delve deeper into the digital realm, the relevance of safeguarding information systems becomes increasingly apparent. The landscape is fraught with digital dangers, which necessitate a strategic approach to fortifying defenses. Ensuring data integrity and maintaining robust security protocols can help mitigate the impact of potential cyber threats. By leveraging advanced technology like artificial intelligence in the defense strategy, organizations can enhance their capability to predict and respond to attacks. Thus, recognizing the critical nature of cybersecurity practices is essential for anyone navigating today’s interconnected world.
Understanding Cybersecurity Threats
In today’s highly connected world, understanding the various cybersecurity threats is essential for both individuals and organizations. Cyber threats can range from simple phishing scams to sophisticated ransomware attacks that can cripple entire systems. By comprehensively analyzing these threats, organizations can better prepare themselves against potential breaches that can lead to significant financial losses and data theft. The dynamic nature of cyber threats requires constant vigilance and adaptation of security strategies.
Cybersecurity threats also include insider threats, where employees unintentionally expose sensitive information, as well as external threats from hackers and cybercriminal groups. The landscape of these threats is continuously evolving, demonstrating the importance of not only recognizing the current risks but also anticipating future challenges. Being proactive rather than reactive is key, as waiting to respond after an attack can lead to devastating consequences.
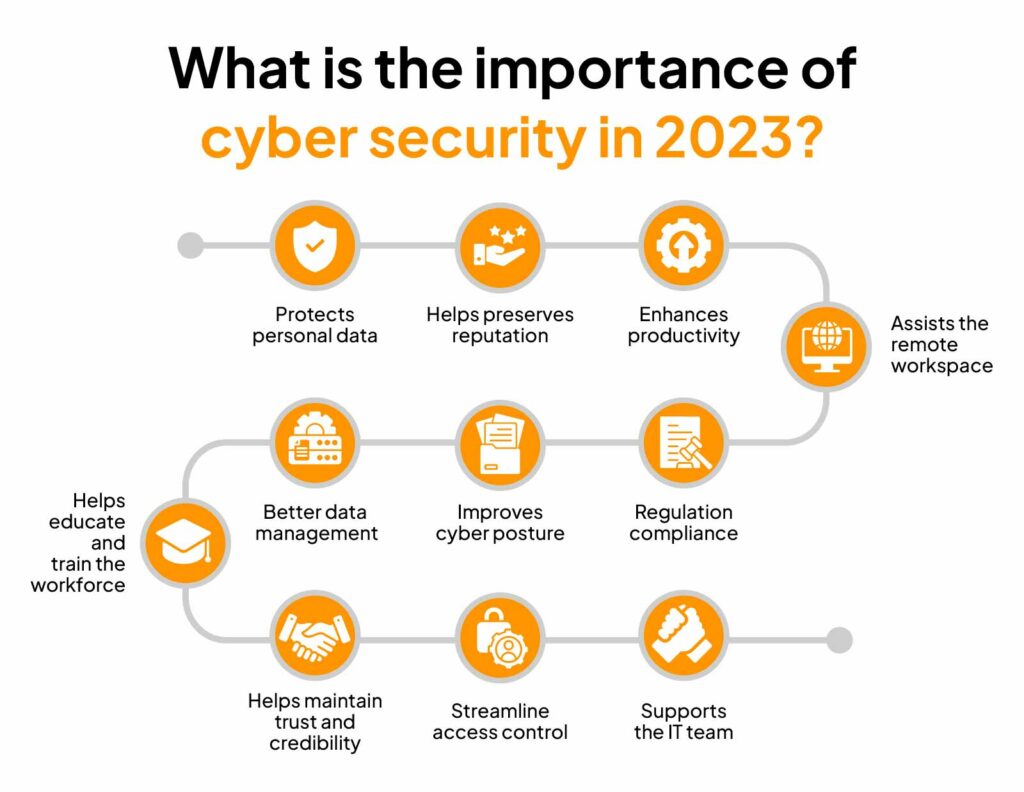
The Importance of Cybersecurity
The importance of cybersecurity in our modern world cannot be overstated. With technology permeating every aspect of life, businesses and individuals alike must prioritize the protection of their digital assets. Cybersecurity helps safeguard personal and sensitive information from malicious actors seeking to exploit vulnerabilities. When organizations invest in robust cybersecurity protocols, they ensure that both their operations and customer trust are maintained.
Furthermore, the integration of cybersecurity into the culture of a business is essential. Employees must not only understand the reactive measures but also the preventive strategies, such as best cybersecurity practices, that minimize risks. This cultural shift underlines the significance of ongoing training and education on cyber hygiene, empowering employees to take ownership of their digital security and form an effective frontline against cyber threats.
Best Cybersecurity Practices for Businesses
Implementing the best cybersecurity practices is crucial for protecting sensitive data and infrastructure within a business. Regular software updates, strong password policies, and employee training are foundational aspects that cannot be overlooked. These practices help close security gaps and ensure that everyone in the organization is aware of their role in maintaining a secure digital environment. A multi-layered security strategy that includes network monitoring and incident response plans can further enhance protection.
Additionally, businesses must foster a culture of cybersecurity awareness among all employees. This includes understanding phishing scams, recognizing suspicious activity, and promoting the use of secure protocols for data transmission. The sharing of these best practices creates a unified front against cyber threats, making it more difficult for cybercriminals to breach defenses. Investing in cybersecurity is not merely a technical necessity; it’s a critical business strategy that can safeguard an organization’s future.
The Role of AI in Cybersecurity
Artificial Intelligence (AI) has a transformative role in the cybersecurity landscape, offering both advantages and potential vulnerabilities. AI technologies can enhance threat detection and response time, processing vast amounts of data to identify patterns that may signal an impending attack. Moreover, machine learning algorithms can adapt to emerging threats, providing businesses with a robust defense system that evolves in real time.
Conversely, the rise of AI also poses new challenges, as cybercriminals can exploit these technologies to craft more sophisticated attacks that may evade traditional detection methods. It is essential for organizations to stay abreast of AI developments in cybersecurity and implement advanced security measures to counteract these evolving threats. Thus, understanding the intersection between AI and cybersecurity allows businesses to leverage technological advancements while fortifying their defenses against increasingly innovative cyber threats.
Practicing Good Cyber Hygiene
Good cyber hygiene is the practice of maintaining a healthy online presence by implementing preventative measures to protect personal and organizational information. Key practices include using strong, unique passwords, enabling two-factor authentication, and regularly updating software to fix security vulnerabilities. These actions help create a formidable barrier against unauthorized access, reducing the likelihood of data breaches and identity theft.
Moreover, being cautious about the information shared online is a fundamental aspect of good cyber hygiene. Individuals and businesses should regularly assess their digital footprint and limit exposure to potential threats. By embracing good cyber hygiene habits, one can significantly diminish risks and foster a secure digital ecosystem, ultimately contributing to a safer online experience for everyone.
Staying Informed on Cybersecurity Trends
Staying informed on current cybersecurity trends is paramount for anyone looking to protect their data and infrastructure. The rapid evolution of technology brings new vulnerabilities, and keeping pace with these changes enables individuals and businesses to adapt their security measures accordingly. By paying attention to cybersecurity news, attending workshops, or subscribing to relevant publications, organizations can remain vigilant against emerging threats.
Additionally, networking with cybersecurity professionals can provide invaluable insights into the best practices and innovative solutions being adopted across the industry. Engaging with communities that focus on cybersecurity awareness helps promote a culture of security and ensures that everyone plays a part in defense strategies. Continued education and awareness are vital components for reinforcing your security posture and combating potential cyber threats effectively.
Cybersecurity for Individuals: Protecting Personal Data
For individuals, protecting personal data is essential in today’s digital age. Cyber threats such as identity theft and phishing attacks can lead to dire consequences, which makes it crucial to adopt measures that safeguard personal information. Utilizing strong passwords, being vigilant about sharing personal details, and reviewing privacy settings on social media can help mitigate the risk of unauthorized access to sensitive data.
Moreover, individuals should embrace tools that enhance their cybersecurity, such as Virtual Private Networks (VPNs) and antivirus software. Regularly updating devices and being cautious of suspicious links or emails can significantly reduce the chances of falling victim to cybercrime. Collectively, these strategies contribute to a more secure online presence and empower users to take charge of their cybersecurity.
Creating a Cybersecurity Plan for Organizations
Creating a comprehensive cybersecurity plan is vital for any organization looking to safeguard its data and operations. A thorough assessment of potential vulnerabilities must be conducted, identifying critical assets and the potential threat landscape. From there, organizations can establish protocols and implement security measures that address specific risks tailored to their operations, such as advanced firewalls and data encryption.
Furthermore, a well-structured cybersecurity plan should include employee training programs that emphasize the importance of cybersecurity awareness. Regular drills and simulations can help familiarize staff with security protocols, ensuring they are prepared in case of an actual breach. A proactive approach in creating and updating the cybersecurity plan will contribute significantly to minimizing potential damage from cyber threats.
The Future of Cybersecurity: Challenges and Innovations
As technology advances, the future of cybersecurity presents both challenges and opportunities. Emerging technologies such as the Internet of Things (IoT) and artificial intelligence are changing the landscape of cyber threats. While these innovations bring convenience and efficiency, they also introduce new vulnerabilities that cybercriminals can exploit, making it essential for cybersecurity practices to evolve in tandem with technology.
On the flip side, these advancements also provide avenues for developing stronger defense mechanisms. Innovations in AI and machine learning can lead to more sophisticated security measures that not only detect threats more efficiently but also predict and mitigate potential attacks before they occur. Embracing these technologies while remaining cognizant of emerging cyber threats will play a crucial role in shaping a safer digital future.
Frequently Asked Questions
Why is the importance of cybersecurity critical for businesses today?
The importance of cybersecurity for businesses is critical because it protects sensitive data from ever-evolving cybersecurity threats. By implementing best cybersecurity practices like regular software updates and employee training, businesses can shield themselves from costly data breaches and maintain customer trust.
What are common cybersecurity threats that individuals should be aware of?
Common cybersecurity threats include phishing attacks, ransomware, and data breaches. Understanding the importance of cybersecurity helps individuals recognize these threats and adopt proactive measures like good cyber hygiene to protect their personal data.
How can protecting data enhance an organization’s cybersecurity posture?
Protecting data is a fundamental aspect of cybersecurity. By implementing encryption, access controls, and regular backups, organizations improve their cybersecurity posture and reduce the risk of falling victim to cyberattacks.
What role does AI in cybersecurity play in combating cyber threats?
AI in cybersecurity plays a dual role; it enhances threat detection and response capabilities, making systems smarter against recurrent attacks. However, it also empowers cybercriminals to automate attacks. Therefore, understanding its importance is crucial for effective cybersecurity strategies.
What are some best cybersecurity practices individuals should follow?
Some best cybersecurity practices include using strong, unique passwords, enabling two-factor authentication, and staying informed about the latest cybersecurity threats. These practices are essential for maintaining good cyber hygiene and protecting personal information.
How can promoting good cyber hygiene help mitigate cybersecurity threats?
Promoting good cyber hygiene, such as cautious sharing of personal information and regular password updates, is vital in mitigating cybersecurity threats. By fostering a culture of awareness and responsibility, individuals can significantly lower their risk of cyber exposure.
What is the importance of regular software updates in cybersecurity?
The importance of regular software updates in cybersecurity lies in their ability to patch vulnerabilities that cybercriminals exploit. Keeping software up-to-date is one of the most effective ways to protect systems from known cybersecurity threats.
Why should organizations invest in cybersecurity training for employees?
Organizations should invest in cybersecurity training for employees because human error is a leading cause of security breaches. Training helps employees recognize the importance of cybersecurity and equips them with the skills to identify and respond to potential threats.
| Key Point | Description |
|---|---|
| Evolving Threat Landscape | Technology advances rapidly, increasing vulnerabilities that malicious actors can exploit. |
| Proactive Cybersecurity | Organizations must implement regular software updates, strong passwords, and employee training. |
| AI in Cybersecurity | AI can improve security but also be misused by criminals to perpetrate attacks. |
| Good Cyber Hygiene | Individuals should use two-factor authentication and be careful with personal information online. |
| Collaborative Efforts | Prioritizing cybersecurity is essential for creating a safer digital environment. |
Summary
The importance of cybersecurity is more significant than ever in our increasingly digital world. With the proliferation of cyber threats and incidents, it is crucial for individuals and organizations alike to prioritize their online safety measures. By adopting proactive strategies, such as robust security practices and staying informed about emerging technologies, we can collectively reduce the risk of cyber threats. In conclusion, fostering a culture of cybersecurity awareness not only protects sensitive information but also helps secure a safer future for everyone.