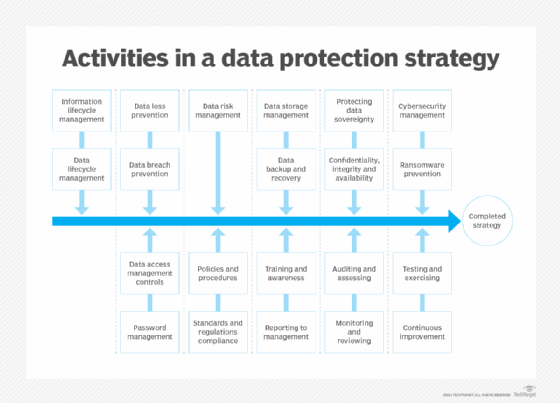
In a world where technology evolves rapidly, effective data protection strategies are essential for safeguarding sensitive information. The constant threat of data breaches has made data privacy best practices more crucial than ever before. Organizations and individuals alike must learn how to protect personal data through robust frameworks and proactive measures. This includes understanding GDPR compliance tips and utilizing innovative data security solutions. By implementing personal data safeguarding techniques, we can protect our valuable information from unauthorized access and enhance overall privacy.
As technology continues to advance at lightning speed, ensuring the security of our information has become a vital priority. Data safeguarding approaches and strategies are no longer just recommendations; they are necessary components of responsible digital citizenship. In today’s environment, understanding how to secure sensitive information is paramount for both businesses and individuals. The integration of various data privacy measures, particularly in light of rigorous regulations like GDPR, is crucial to minimizing risks. In this article, we will delve into effective methodologies and considerations for securing personal data against evolving threats.
Understanding Data Protection Strategies
Data protection strategies form the backbone of a secure digital environment, particularly as organizations struggle to keep pace with evolving technologies. These strategies involve a comprehensive range of practices tailored to minimize the risks associated with data breaches. Fundamental to these strategies is the collection and processing of personal data in a manner that respects user privacy, ensuring compliance with regulations like GDPR. By addressing data protection proactively, businesses can safeguard sensitive information and foster trust among their customers.
To create effective data protection strategies, organizations should conduct regular risk assessments to identify vulnerabilities in their data handling processes. This includes implementing encryption methods, access controls, and secure data storage solutions, which together form a robust defensive barrier against potential threats. Moreover, ongoing employee training on data privacy best practices is crucial, as human error remains a significant factor in data breaches.
Best Practices for Data Privacy
Embracing data privacy best practices is essential for any organization aiming to protect personal data. At the forefront of these practices is transparency with users—informing them about how their data is collected, used, and shared is vital in fostering a trustworthy relationship. Furthermore, organizations should ensure that privacy policies are clear and accessible, empowering users to make informed choices about their personal information.
In addition to transparency, implementing strong data security solutions is critical. This encompasses adopting advanced technologies such as two-factor authentication, which significantly enhances the security of personal accounts. Regular audits of data handling practices and compliance with GDPR guidelines not only help to mitigate risks but also enhance the overall organizational reputation. Understanding how to protect personal data extends beyond mere compliance, as organizations are encouraged to create a culture of privacy.
GDPR Compliance Tips for Organizations
Complying with GDPR is crucial for businesses operating in or with clients in Europe, and it starts with understanding the fundamental principles of the regulation. GDPR emphasizes the need for lawful processing of personal data, which necessitates obtaining explicit consent from users before data collection. Organizations should consider incorporating privacy-by-design principles, ensuring that data protection measures are integral to the development of new products or services.
Moreover, organizations must appoint a Data Protection Officer (DPO) to oversee compliance efforts and handle data protection queries. Regular training sessions related to GDPR compliance tips for employees can also significantly improve awareness and adherence to data protection laws. By staying informed about regulations, businesses can better navigate the complexities of data privacy, ensuring that they uphold consumers’ rights while mitigating the risks of data breaches.
Effective Data Security Solutions
To combat the rising tide of cyber threats, implementing effective data security solutions is paramount. These solutions encompass a variety of tools and technologies designed to protect sensitive data against unauthorized access, corruption, or theft. Key components include firewalls, intrusion detection systems, and antivirus programs, which collectively create layers of defense against potential attacks.
In addition to technology, the role of employee training cannot be overstated. Organizations must invest in ongoing education to equip staff with knowledge about potential security threats and personal data safeguarding techniques. Regularly updating data security protocols and software systems also plays a vital role in staying ahead of cybercriminals and ensuring the integrity of personal data.
Personal Data Safeguarding Techniques
Personal data safeguarding techniques are essential for ensuring privacy and protecting individuals’ sensitive information. These techniques involve using various strategies, including data masking, which obscures specific data within a database to protect it from unauthorized access. Moreover, implementing robust logging and monitoring systems can help organizations detect and respond to suspicious activities in real time, fostering a safer data environment.
Another key aspect of personal data safeguarding includes the regular assessment of third-party vendors and partners who have access to organizational data. Ensuring that these entities adhere to strong data protection practices is crucial for maintaining overall data security. By continuously evaluating and reinforcing personal data safeguarding techniques, organizations can significantly reduce the risk of data breaches, ensuring the trust and confidence of their clients.
The Importance of Data Privacy Awareness
Data privacy awareness is increasingly important as our lives become more intertwined with technology. Consumers must understand their rights regarding personal data and the implications of sharing information online. By fostering awareness, organizations can empower individuals to make informed decisions about their data, leading to better protection practices both personally and institutionally.
On the organizational side, creating a culture of data privacy awareness within the workplace enhances security protocols and reduces the likelihood of human error causing data breaches. Regular workshops, newsletters, and updates regarding data protection strategies help keep privacy at the forefront of organizational practices. It is essential that everyone, regardless of position, understands the impact of their actions on data privacy and security.
Implementing Robust Data Encryption
Implementing robust data encryption is a crucial step in securing personal data and ensuring compliance with data protection regulations. Encryption transforms sensitive data into unreadable code, accessible only by those with the correct decryption key. This ensures that even if data is intercepted or accessed unlawfully, it remains secure and meaningless without the corresponding key.
In addition to initial encryption methods, organizations should regularly review their encryption practices, considering newer, more advanced algorithms to equip their systems against evolving threats. Additionally, educating employees about the importance of using encryption for data shared internally and externally can bolster an organization’s defenses against data breaches.
The Role of Technology in Data Protection
Technology continues to play an increasingly vital role in data protection as threats evolve. Utilizing cutting-edge software solutions that employ machine learning and artificial intelligence can enhance data security by anticipating and identifying potential breaches before they occur. These technologies provide organizations with proactive data protection strategies that evolve alongside new threats.
Moreover, incorporating cloud-based storage solutions offers enhanced security features such as automatic backups, encryption, and compliance tracking. By harnessing these technological advancements, organizations can efficiently manage their data protection efforts, ensuring sensitive customer information is safeguarded against unauthorized access or breaches while demonstrating a strong commitment to data privacy.
Monitoring and Auditing Data Practices
Monitoring and auditing data practices are essential components in maintaining a secure data environment. Organizations should establish regular review processes that evaluate both internal and third-party data management practices. This proactive approach allows organizations to identify compliance gaps and areas requiring enhancement, preventing potential data breaches before they happen.
In addition to monitoring data use and storage, auditing access logs and user activities provides insight into how data is being utilized across the organization. These audits not only ensure compliance with data protection regulations but also help organizations understand their data flow better, allowing for more informed decision-making regarding data security investments and protocols.
Frequently Asked Questions
What are the best data protection strategies for businesses?
Implementing data protection strategies such as data encryption, access controls, and regular security audits are essential for businesses. Additionally, training employees on data privacy best practices ensures everyone understands their role in safeguarding personal data.
How can individuals protect their personal data online?
Individuals can protect their personal data by using strong passwords, enabling two-factor authentication, and being cautious of sharing information on social media. Following personal data safeguarding techniques like regularly updating software and using privacy-focused tools can further enhance data security.
What are the key GDPR compliance tips for organizations?
Key GDPR compliance tips include conducting data protection impact assessments, obtaining explicit consent for data collection, and ensuring transparency in data processing activities. Organizations should also provide training on data privacy best practices to all employees.
What data security solutions can help reduce the risk of data breaches?
Data security solutions such as firewalls, intrusion detection systems, and encrypted cloud storage can significantly reduce the risk of data breaches. Regularly backing up data and monitoring for suspicious activities are also crucial components of effective data protection strategies.
How can companies develop a culture of data privacy among employees?
Companies can foster a culture of data privacy by providing ongoing training on data protection strategies and encouraging open discussions about data safeguarding techniques. Establishing clear policies and accountability measures also helps reinforce the importance of data privacy in the workplace.
What are some effective personal data safeguarding techniques?
Effective personal data safeguarding techniques include minimizing the amount of personal data collected, routinely reviewing data access permissions, and swiftly addressing any reported data security incidents. Staying updated on the latest data privacy trends also aids in enhancing overall data protection.
What role does training play in data protection strategies?
Training plays a vital role in data protection strategies by equipping employees with knowledge about potential data security threats and the importance of adhering to data privacy best practices. Regular training sessions can greatly enhance an organization’s ability to safeguard personal data effectively.
How can encryption help in protecting personal data?
Encryption helps protect personal data by converting it into a coded format that is unreadable to unauthorized users. By integrating data encryption as part of data security solutions, organizations can significantly reduce the risk of data breaches and ensure compliance with data protection regulations.
Why is it important to regularly update data protection strategies?
Regularly updating data protection strategies is crucial due to constantly evolving technology and emerging cybersecurity threats. Staying informed about the latest data security solutions and revisions in regulations, such as GDPR, ensures organizations maintain effective safeguards for personal data.
What steps should be taken to ensure compliance with data privacy laws?
To ensure compliance with data privacy laws, organizations should conduct regular audits of their data processing activities, implement policies that align with GDPR compliance tips, and maintain clear documentation of consent from users. Employing data protection strategies tailored to legal requirements also plays a critical role.
| Key Point | Description |
|---|---|
| Importance of Data Privacy | The rapid evolution of technology has heightened concerns about data privacy for both individuals and organizations. |
| Data Breaches | Numerous data breaches are commonly reported, stressing the need for better protective measures. |
| Regulatory Landscape | New regulations like GDPR emphasize the importance of compliance and proactive data management practices. |
| Best Practices | Implementing effective data protection strategies is essential for safeguarding personal information. |
Summary
Data protection strategies are critical in today’s fast-paced digital landscape. Understanding the risks associated with data breaches and adhering to regulatory requirements like GDPR underscores the necessity for robust protective measures. Organizations and individuals alike must prioritize implementing best practices to secure personal data against the evolving threats in this environment.